Online Generic SQL Injection Vulnerability Scanner
Detect SQL Injection vulnerabilities in your web applications
Short Info
Level
Single Scan
Single Scan
Can be used by
Asset Owner
Estimated Time
30 minutes
Time Interval
1 month 18 days
Scan only one
URL, Request
Toolbox
Online SQL Injection Tool
With free and online SQL injection scanning tool, you can scan SQL Injection vulnerabilities for query parameters sent with the HTTP GET,POST,PUT,DELETE methods. Furthermore, you can either export this scan's result as PDF or watch all scanning processes as video.
For example, this SQL Injection tool parses param1 and param2 parameters and test for sql vulnerability for a url such:
https://s4e.io/demopage?param1=value1¶m2=value2
If you want to perform SQL injection vulnerability tests with POST parameters, on this page, forms that communicate with POST requests within a web page are automatically parsed and all parameters are tested with the SQLmap tool.
By analyzing your web page, we find the forms that communicate with the POST request and look for SQL Injection vulnerabilities in these form parameters.
Due to ethical concerns, you should verify that your website belongs to the site when checking for this vulnerability.
You can read the rest to get more detailed information about the vulnerability.
What is SQL Injection Vulnerability?
In dynamic pages in web applications, the information presented to the user is often served by reading from databases. Reading from the database is performed within database-specific rules. Databases in which data are stored relationally in accordance with predetermined templates (table structures) are called relational databases. Structured Query Language (SQL) is a programming language for managing data in relational databases.
In web applications, user-received values can be included in SQL queries in some cases. The queries created by using the parameters received from the user in statements are called dynamic SQL queries. For example, in order to search, the value to be searched must be obtained from the user. Similarly, in order to paginate, it is not possible to read the relevant data from the database without obtaining the number of the page that the user wants to view. So statements are used in these types of queries called dynamic.
The attacks by interfering with dynamic SQL statements running on the target system are called SQL Injection attacks, and the resulting vulnerability itself is called SQL Injection Vulnerability.
By triggering this vulnerability, cyber attackers can perform many different malicious operations, from gaining information about the database, accessing database administrator passwords, deleting and capturing data, running custom SQL statements in the database, and even running commands in the operating system by interfering with SQL queries.
SQL Injection vulnerabilities are the vulnerabilities that occur when the inputs from the user are used in SQL queries without filtering them correctly. The vulnerabilities are divided into sub-categories according to the triggering method. We have listed all the categories we could find by scanning the academic literature below:
- TAUTOLOGY
- LOGICALLY INCORRECT
- BLIND SQL INJECTION
- TIME-BASED BLIND
- BOOLEAN-BASED BLIND
- STORED PROCEDURES
- PIGGYBACKED
- QUERY AND UNION QUERY
- INLINE QUERIES
- STACKED QUERIES
- ERROR-BASED
- UNION QUERY-BASED
Some of these categories are actually used for vulnerabilities of the same type. 6 of them are categories included in open-source software called SQLmap, which we also use in our SQL injection scanner tool.
- BOOLEAN-BASED BLIND
- ERROR-BASED
- UNION QUERY-BASED
- STACKED QUERIES
- TIME-BASED BLIND
- INLINE QUERIES
Let's take a look at these.
In blind SQL injection vulnerabilities, attackers cannot directly interfere with any data on the target system. Instead, attackers exploit this type of vulnerability by delaying the response from the server (time-based), or by converting some behaviors in the returned response into a state (true/false).
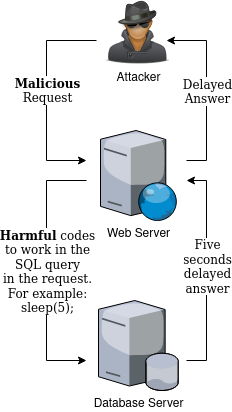
Figure 1.4.2.1 Blind SQL Injection (Time Based Example)
Union is a special expression that combines two different queries to return a single answer. In Union-based SQL Injection attacks, real SQL query and the SQL query sent by the attacker combined (like select col1, col2 from table union select col1, col2 from other_table). Therefore database run both valid and malicious query and return the answer.
In the Stacked-based (piggy-backed) SQL Injection vulnerability, the attacker sends an independent query to the target system, allowing its own query to run after the first query that exists on the target system (like select * from table;select password from users;) . Such vulnerabilities may not work in every database and web application. For example, the sequential execution of more than one SQL query at a time is turned off by default in some frameworks.
In error-based SQL Injection attacks, the attacker sends the payload to the target system that will cause errors in database queries. The resulting error leaves a trace in the body or headers in the returned response. By looking at this trace, the attacker can collect the necessary information on the target system.
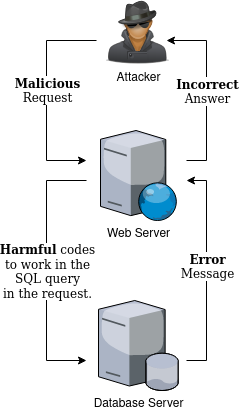
Figure 1.4.2.2 Error Based SQL Injection
In the type of inline queries, SQL Injection vulnerabilities, as the name suggests, are vulnerabilities where SQL queries are manipulated using inline queries. The attacker forces the system to work in its own interests by injecting the SQL queries it uses into real SQL queries.
If there is a connection you suspect, you can use this tool that tests the SQL Injection vulnerability for your web application.
In order to be able to scan in the most accurate way, it is recommended to disable methods such as captcha, rate limiting.